Towards a better approach for Quantum-Key-Distribution (QKD) Networks key management

Powerful Quantum Computers represent a risk to traditional security. They have the potential to break the currently used cryptography. Despite the fact that quantum computers with such a capacity are foreseen to arrive in the next 10 years, valuable data can already be exposed. The secure communications can be recorded now and decrypted with a quantum computer in the future. Quantum-key-Distribution (QKD) can be used to securely exchange cryptographic keys among different communication parties by using QKD nodes (also known as “trusted nodes”). Usually, trusted nodes integrate QKD modules and a distributed key manager, which demands the meeting of strong security requirements. Different architectural choices of the quantum network might relax the security requirements of the trusted nodes. In this article we discuss our findings on the role of a centralized key manager and the effect on the relaxation of the security restrictions of the trusted nodes so as to better and more efficiently use the QKD technology.
The EuroQCI (European Quantum Communication Infrastructure) initiative
EuroQCI is a European initiative towards the implementation of an ultra-secure communication infrastructure, resistant to classical and quantum attacks, which is based on quantum technologies for the protection of European assets including its overseas territories. EuroQCI is deployed through terrestrial and space connectivity. The first service of the EuroQCI is the Quantum Key Distribution (QKD), being able to perform the secure key exchange among communication parties. These keys can be used by users to perform different security functionalities. In the future, the EuroQCI could be updated to support the future quantum Internet.
“By using quantum channels, the information encoded as quantum states can be exchanged. An attacker cannot clone nor eavesdrop the channel without being noticed”, says Philippe Barbier, Head of Systems & Satcom Services Programs, AIRBUS Defence and Space. This is especially attractive for users that require key exchange with a high security level.
The European Commission selected in 2021 the consortium OQTAVO, led by Airbus and composed by eight partners to design the end-to-end EuroQCI architecture. It included Airbus Defence and Space, Airbus Cyber, Leonardo, Orange, PwC France and Maghreb, Telespazio (a Leonardo and Thales joint venture), the Consiglio Nazionale delle Ricerche (CNR) and the Istituto Nazionale di Ricerca Metrologica (INRiM). Results were successfully delivered to the European Commission on July 2022.
In January 2023, 26 National Quantum Communication Infrastructures (NatQCIs) across 26 EU Member States started to be planned and deployed. It is expected that in 2027 the EuroQCI can be demonstrated.
From Quantum links to Quantum Networks
QKD is one of the building blocks of the overall information security infrastructure. The QKD is used to generate and distribute cryptographic keys. In contrast with traditional approaches, the security does not rely on the hardness of mathematical problems, but on the properties of physics. To exchange a key, transmitter (Alice) and receiver (Bob) QKD modules are connected by a quantum link composed by:
Quantum channel, that transmits quantum information encoded as photons through a direct optical fiber or free-space link; and
Public channel, for further supporting and post-processing of the exchanged information.
These modules are able to establish the same secret key at both sides (KA, KB). In order to establish these quantum-secure keys, QKD nodes that host QKD receiver/transmitter modules are used. As there are not yet quantum memories, the quantum information at the receiver is measured and stored in a classical buffer at each QKD node. At this state, the quantum advantage disappears and information is prone to be copied, thus QKD nodes need to be secure. These nodes are usually called trusted nodes and should be encapsulated into a secure boundary so as to prevent any tampering.
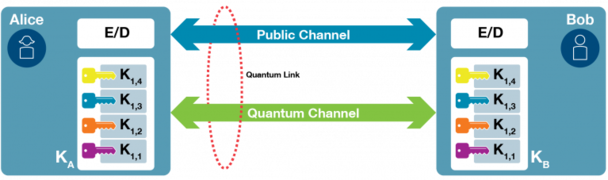
Figure 1. Two QKD modules.
The key sets established at Alice and Bob (KA , KB ) are identical
Quantum networks integrate a set of trusted nodes to widely distribute QKD keys to end users, which are in the capacity to employ the keys to implement different security functionalities. The functional structure of the quantum network is based on a layered approach to ease its programmability, the flexibility and the virtualization capabilities as defined in different standards.
Four layers can be identified:
Control Layer, defining the routes of the quantum material between the end-users;
Management Layer, monitoring and controlling the health and security and capacity of the system;
Key Management layer, implementing functionalities required to support the key lifecycle. It includes relaying the keys across the network, and supplying the keys to cryptographic applications.
Quantum and optical layer, including the quantum and optical devices required for establishing the optical and quantum links.
Usually each trusted node integrates different QKD modules (transmitter/receiver) and a key manager (KM) [REF Fig2] to implement the functionalities of the key management layer. It includes synchronization and re-formatting of agreed bit strings and key storage in the trusted node. In a quantum network, each KM relays key material through a KM link in an encrypted way (e.g., One-Time-Pad). Once the keys are used, they are discarded. Note that a distributed KM forces the transmission of sensitive information through the different trusted nodes. The neighbor trusted node has part of the secret and can infer the value of the previous keys. As a consequence, strong security boundaries should be put in place and the user should fully trust the infrastructure or complex key derivation functions to strongly encrypt the KM link should be used and the complexity of the network is increased.
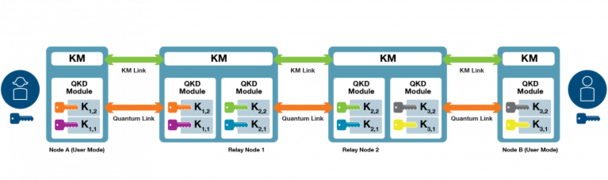
Figure 2. Each QKD node integrates a QKD module and the key manager (KM) which relays keys in an encrypted manner to the next QKD node.
A fully distributed KM approach imposes strong security requirements at each trusted node. The capture of a trusted node might leak critical information. Thus, the cost of the infrastructure to secure these nodes can be high.
Innovation
OQTAVO-EuroQCI explored different quantum network architectural solutions. Among the different alternatives, our innovative centralized Key management for QKD shows attractive security properties. In this approach, the quantum-secure material generated by the QKD nodes is used to create secure masks (e.g., C1x[REF Fig3]). That is, during the creation of the masks, they were not copied and not eavesdropped. These masks are used to transport a secret key (S) generated at Alice’ side in a quantum-secure way. The masks generated in the different trusted nodes are collected by the centralized Key Manager (note that this is a logically centralized element and can be implemented in different ways) to encrypt the secret key (s). An XOR is used (i.e., OTP) but any other cryptographic transformation can be employed (e.g., AES, Post-quantum Cryptographic primitives). If a trusted node is compromised by an attacker and a mask is captured, the secret (s) will not be retrieved neither by Bob nor the attacker. As no sensitive information is being exchanged through the trusted nodes (i.e., the secret s), the security requirements of the trusted node can be relaxed. The key manager should remain secure. Nevertheless, different techniques to ensure the security of the key management to the highest level of security are already known and used in the real world.
This centralized key relay approach strongly protects the key material, since only trusted nodes located at the user side (User Nodes Alice and Bob) have access to the key material in the clear. Also note that different key derivation functions that can be used to generate more elaborate masks can be used, providing different security properties to the transported secret key.
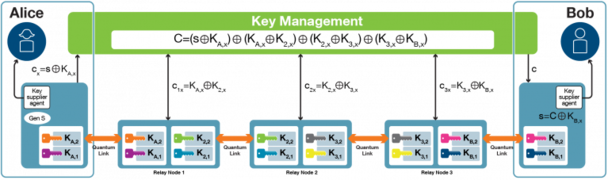
Figure 3. Use of a centralized Key management scheme for QKD.
This is a logical view. The user key material (s), securely generated in the Node A, is XOR-ed with KA,x, and sent to the XOR collectors in the Key Manager. Note that different key derivation functions can be used for secure Cx. As shown, only the Node B can recover the secret key (s). The Key Manager allows to precompute the data necessary to relay the key using a certain route. In this way the key relay can be even more efficient.
In contrast with the fully distributed approach, our proposal allows the relaxation of the security requirements on the trusted nodes. When a QKD node is compromised, the information gained by an attacker is not enough to retrieve the secret (since this information is only used for masking purposes). The key management layer, implemented with traditional technology, can be secured using different widely known techniques.
Conclusion
We believe that quantum communication is a key building block for the quantum-secure era. The QKD and post-quantum cryptography are relevant security primitives that exhibit different properties and that are expected to work together to ensure the wide quantum-resistant protection. We think that using a logically centralized Key Manager will ease the secure adoption of the QKD technology for different applications and will ease the certification processes. The complete technical description of this approach will be soon published in a scientific article.